Node.js 12.8.1 (64-bit)
從當前電子郵件客戶端切換到 eM Client 不會更容易,因為您可以直接導入所有數據 Microsoft Outlook,Mozila Thunderbird,蝙蝠或 Windows 的郵件,所以你可以在幾分鐘內開始。此外,您還可以輕鬆將所有數據導出到許多可用的格式,或製作和恢復備份.
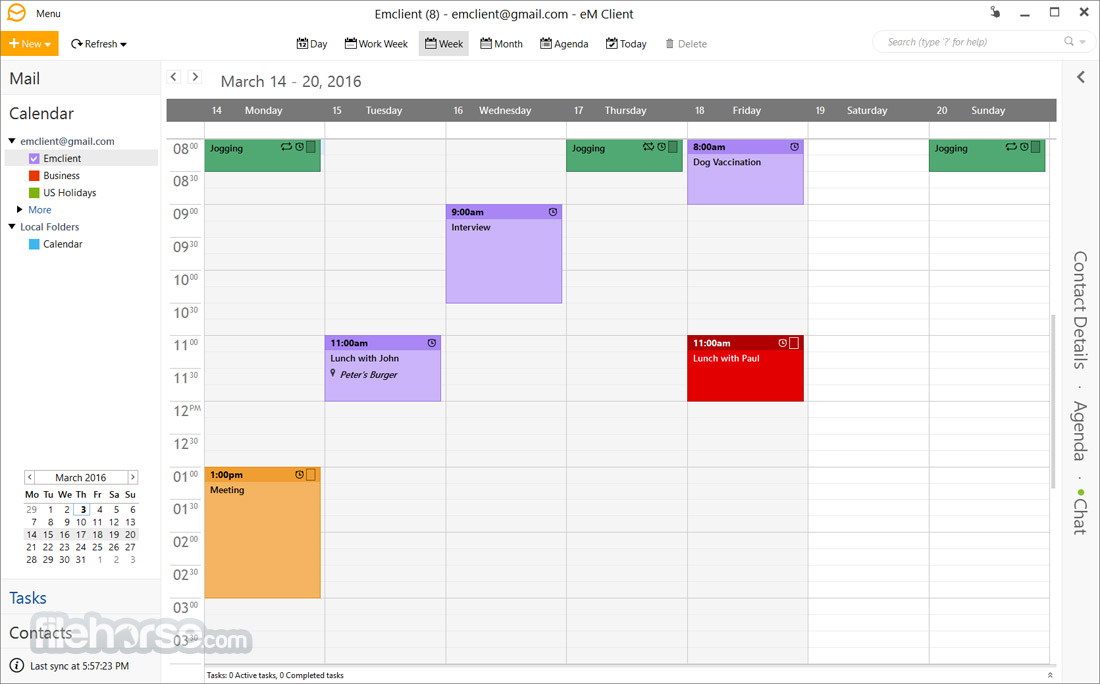
用戶界面非常乾淨,現代化,可定制且直觀。 eM Client 本地化到 19 種語言和 10 多彩主題。默認的“現代”主題是非常好的,但你可以根據你的顏色偏好來改變它。左側邊欄為您提供了對您的電子郵件帳戶,日曆,任務和聯繫人的訪問權限,並且該權限可以隱藏,而且您可以使用它來訪問聯繫人詳細信息,日程安排和聊天。聊天可以分離到一個單獨的窗口,如果需要的話,它支持三種主要的消息服務:Google Talk 和 Facebook 和 Jabber,並提供文件傳輸。
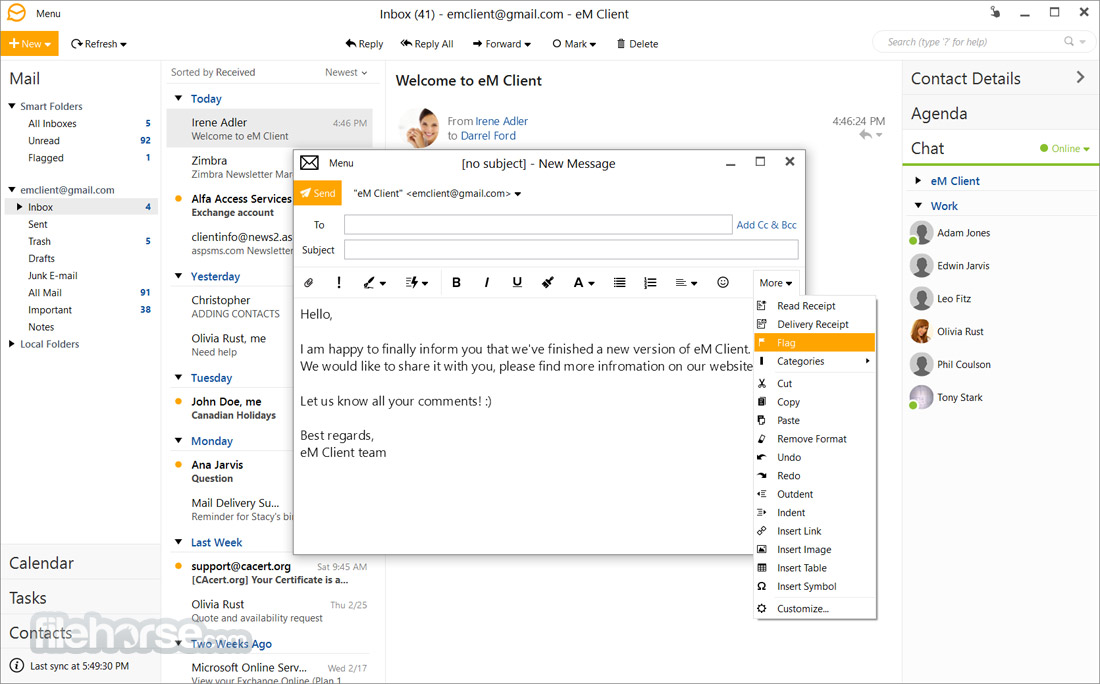
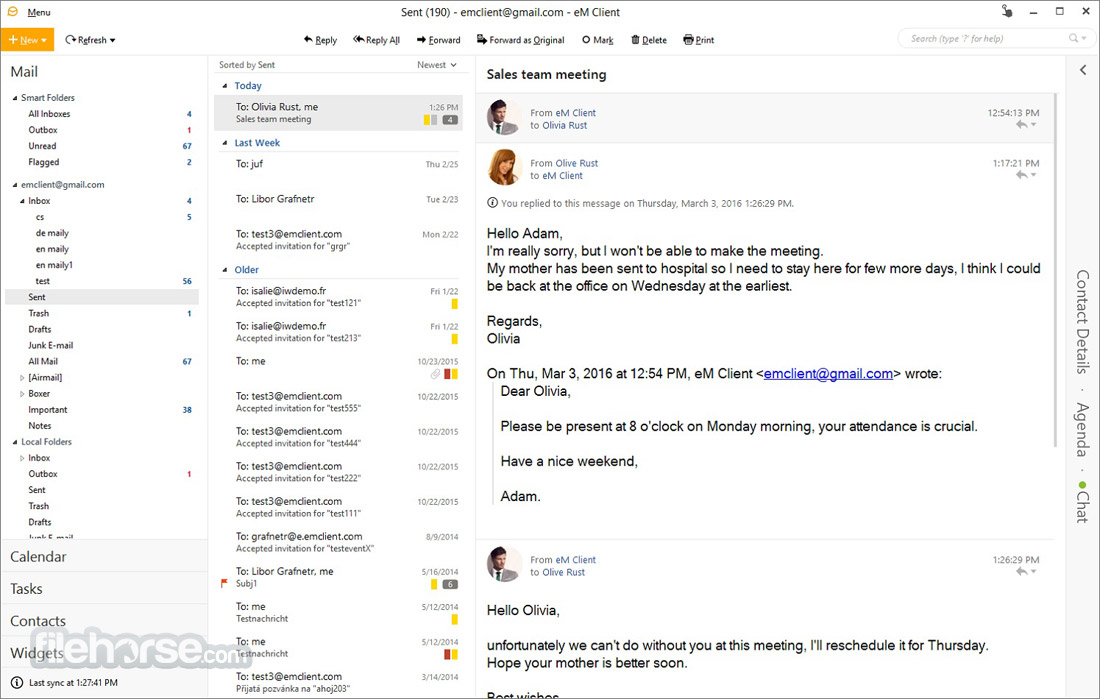
閱讀和發送電子郵件是一種純粹的快樂。您可以在左側或底部設置消息面板或禁用,在這種情況下,當您打開新消息時,它將顯示在新窗口中。搜索速度非常快,並提供準確的結果。一些漂亮的功能是延遲(預定)的電子郵件發送,完整的拼寫檢查,電子郵件模板和簽名,信息加密和創建電子郵件 grops,在哪裡你可以添加更多的人,你想同時發送電子郵件。這可以是非常有用的,可以為您節省大量的時間.
唯一的缺點是它的內存使用率較高(與 Thunderbird 相比),但總體來說,eM Client 最新版本是一個令人印象深刻的電子郵件客戶端,具有許多功能。個人使用最多可以有兩個電子郵件帳戶。如果你需要兩個以上的帳戶(或者如果你需要它用於商業用途),你將不得不購買一個高級版本,並相信我在這一個:在 eM Client 上花的錢將是非常好的錢花費.
eM Client 功能:
PGP 加密支持
eM Client 現在支持 PGP - 創建或導入您的 PGP 密鑰來發送加密和簽名的電子郵件。檢查視頻的說明.
Live 備份
您不必再退出 eM Client 為了進行備份。 eM Client 現在將在運行時備份,因此即使正在運行,您也可以繼續工作.
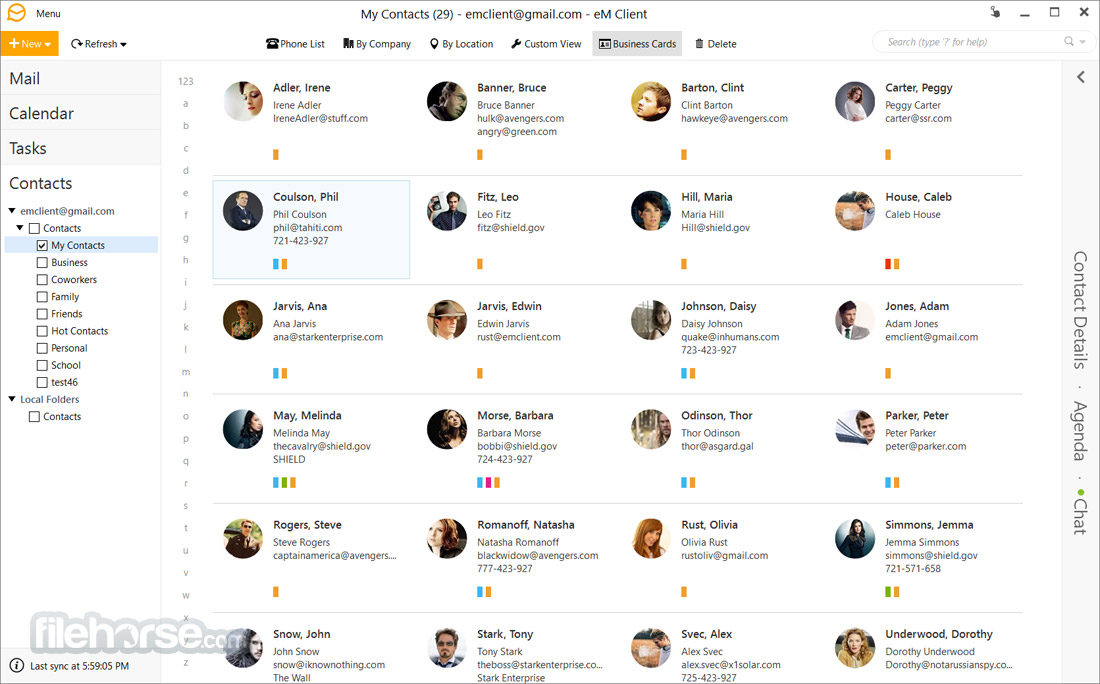
自動聯繫人頭像下載
eM Client 7.1 自動從 Web 下載並顯示聯繫人的頭像。我們從 Gravatar 下載,域圖標等等。
改進的表格編輯器
編輯表格變得簡單多了 - 您可以調整任何單元格,行或列的大小.
超大尺寸和基本編輯圖像
將圖像轉換為電子郵件現在比以往更簡單。他們不僅可以自動調整大小,還可以手動更改大小,還可以旋轉和翻轉大小.
Gmail 的自動回复功能
自動為 Gmail 提供“外出”回复功能。讓每個人都知道,您將無法通過在 eM Client.
注意內配置自動響應來響應他們的電子郵件:需要.NET Framework。在免費版本中,您最多只能添加 2 個賬戶.
ScreenShot
| 軟體資訊 | |
|---|---|
| 檔案版本 | Node.js 12.8.1 (64-bit) |
| 檔案名稱 | node-v12.8.1-x64.msi |
| 檔案大小 | 17.4 MB |
| 系統 | Windows XP / Vista / Windows 7 / Windows 8 / Windows 10 |
| 軟體類型 | 未分類 |
| 作者 | eM Client Inc. |
| 官網 | http://www.emclient.com/ |
| 更新日期 | 2019-08-16 |
| 更新日誌 | |
|
What's new in this version: Fixed: Node.js 12.8.1 (64-bit) 相關參考資料
64-bit - Node.js
沒有這個頁面的資訊。瞭解原因 https://nodejs.org Descarga | Node.js
macOS Installer (.pkg), 64-bit. macOS Binary (.tar.gz), 64-bit. Linux Binaries (x64), 64-bit. Linux Binaries ... Linux on Power Systems, 64-bit. Linux on System z ... https://nodejs.org Download | Node.js
Latest Current Version: 12.8.1 (includes npm 6.10.2). Download the ... macOS Installer (.pkg), 64-bit. macOS Binary (.tar.gz), 64-bit. Linux Binaries (x64), 64-bit. https://nodejs.org Node.js
Download for Linux (x64). 10.16.2 LTS Recommended For Most Users · Other Downloads · Changelog · API Docs · 12.8.1 Current Latest Features. https://nodejs.org Node.js (32-bit) Download (2019 Latest) for Windows 10, 8, 7 - FileHorse
Download Node.js (32-bit) for Windows PC from FileHorse. 100% Safe and Secure ✓ Free Download (32-bit/64-bit) Latest Version 2019. https://www.filehorse.com Завантажити | Node.js
macOS Installer (.pkg), 64-bit. macOS Binary (.tar.gz), 64-bit. Linux Binaries (x64), 64-bit. Linux Binaries ... Linux on Power Systems, 64-bit. Linux on System z ... https://nodejs.org 다운로드 | Node.js
macOS Installer (.pkg), 64-bit. macOS Binary (.tar.gz), 64-bit. Linux Binaries (x64), 64-bit. Linux Binaries ... Linux on Power Systems, 64-bit. Linux on System z ... https://nodejs.org |
|
